The platform supports resource monitoring using Simple Network Management Protocol (SNMP) Traps. You can:
- Create an SNMP Trap for each client.
- Define the resources from which to receive traps.
- Receive traps from devices.
SNMP trap processing
An SNMP trap indicates a specific condition defined in the Management Information Base (MIB) expressed as variable bindings that include a trap message. The platform processes traps and transforms them into alerts.
OID usage
The SNMP Object Identifier (OID) is an address that identifies devices for tracking device status. The SNMP OID has a form such as: 1.3.6.1.6.3.1.1.5.5.
You can include or exclude OIDs when creating an SNMP Trap monitor.
Scenarios
Do not want to receive specific SNMP traps
If you do not want to receive SNMP traps from specific OIDs, create an SNMP trap monitor that excludes the OIDs you do not want to receive the trap from.
Want to receive all SNMP traps
If you want to receive SNMP traps from all resources, create an SNMP trap monitor and select the Receive traps from all devices option.
Want to receive specific SNMP traps
If you want to receive SNMP traps only from specific resources, select the Receive traps from specified devices only option and choose the devices that you want to receive the SNMP traps from.
Want to discard specific SNMP traps
If you want to discard SNMP traps from specific IP addresses, create an SNMP trap monitor and select the Discard traps from specific IP addresses option.
Create an SNMP trap monitor
You can add to the list of SNMP-enabled device traps to monitor:
Go to Setup > Monitoring > SNMP Traps Configuration. This displays a list of any existing SNMP trap monitors, which you can edit, or continue to create a new monitor.
To add a trap monitor and filter, click the + icon.
In Client Name, choose the client.
Enter a unique, descriptive Monitor Name.
Include or exclude specific OIDs you want to monitor by selecting Exclude OID or Include OID and entering the OID.
Note
You can either include OIDs or exclude OIDs you cannot mix including and excluding OIDs. OIDs that are already included or excluded in the SNMP trap monitor are be visible in the Include OIDS list.
If you want to add new OIDs to include or exclude, you can add them manually or import a CSV file.To manually add OIDs to include or exclude:
- Select Exclude OIDs or Include OIDs.
- Click + for each OID you want to add to the include or exclude list.
During the manual entry, you can not add empty, duplicate, or invalid OIDs.
To import a CSV file of OIDs to include or exclude:
Select Exclude OIDs or Include OIDs.
Create a CSV file containing the OIDs. The CSV file has one column with
Oidsas the heading followed by one OID per line after the heading:Oids 1.3.6.1.6.3.1.1.5.3 1.3.6.1.6.3.1.1.5.4Click Choose file to select the CSV file.
Click Upload.
Note
When you upload a CSV file the OIDs in the CSV file replace any OIDs already included or excluded in the SNMP trap monitor.In the Devices section, choose the option for selectively receiving or discarding traps:
Option Description Action Receive traps from all devices Traps are received from all devices. N/A Receive traps from specified devices only Traps are received from selected devices. From the list of Available Devices, select the device and click the right-chevron (>>) to add the device to the Selected Devices category. Receive traps from specified device groups only Traps are received from selected device groups. From the list of Available Device Groups, select the device group (or) groups and click the right-chevron (>>) to add the device groups to the Selected Devices groups category. Discard traps from specific IP addresses Traps are discarded from devices selected by IP address. For traps that you want to discard, enter a comma-separated list of device IP addresses in the List of devices edit box. Click Save to apply your changes and display the list of available SNMP trap monitors:
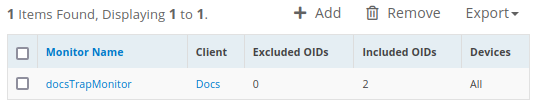
Click the SNMP trap monitor name to change monitoring settings.
To remove an SNMP trap monitor, select the monitor name and click the delete icon.
To export the SNMP trap monitors list as a CSV or PDF file, click Export and select the format.
Note
The Process all Interface traps checkbox has been introduced in SNMP configurations to disable non-monitoring SNMP trap interfaces. The checkbox is set false by default..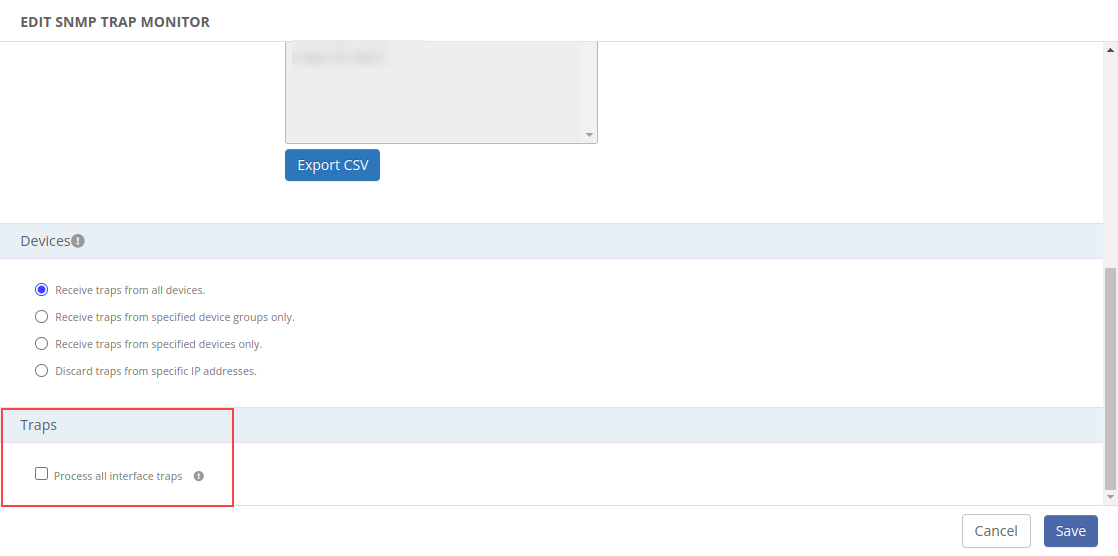
Configuring SNMP v3 Traps
When you configure a gateway as an SNMP Trap receiver, the device-generated traps are sent to the gateway and processed according to the configuration defined when you created the SNMP trap monitor.
For SNMPv2 traps, the gateway can interpret the Trap OIDs because the message is not encrypted. For SNMPv3 traps, the OIDs are encrypted and the gateway needs to know the encryption credentials to decode the traps.
Default SNMPv3 Credentials
By default gateway understands and processes the SNMP v3 Traps if the remote devices use the same credentials pre-defined in the gateway.
If you want to know the list of pre-defined credentials in the gateway then please reach OpsRamp Support Team.
Adding Custom SNMPv3 Credentials
If you prefer not to use the default credentials, you can define your own gateway credentials using Base64 encoding.
Formatting the Custom Credentials
- Define your custom SNMPv3 credentials in the following format:
{securityname}###{authProto}###{authPassPhrase}###{privProto}###{privPassphrase}
Example: user6###MD5###abcdef@123###DES###ghijkl@456- If any of the fields mentioned below are empty or not needed, please use
NONEfor the field value.- authProto
- authPassPhrase
- privProto
- privPassphrase
Below is the format to be followed in the trap configuration file for SNMP protocols:
| Snmp Privacy Protocol | Configuration format |
|---|---|
| DES | DES |
| DES3 | DES3 |
| AES | AES |
| AES128 | AES-128 |
| AES192 | AES-192 |
| AES256 | AES-256 |
| AES192C | AES-192-C |
| AES256C | AES-256-C |
| Snmp Auth Protocol | Configuration format |
|---|---|
| SHA | SHA |
| SHA224 | SHA224 |
| SHA256 | SHA256 |
| SHA384 | SHA384 |
| SHA512 | SHA512 |
| MD5 | MD5 |
For example:
SNMP v3 credentials are AuthPriv then:
snmpusername###MD5###snmpuserauthstring###DES###snmpprivstringSNMP v3 credentials are AuthNoPriv then:
snmpusername###MD5###snmpuserauthstring###NONE###NONESNMP v3 credentials are NoAuthNoPriv then:
snmpusername###NONE###NONE###NONE###NONE
As another example, a device with the following SNMPv3 credentials:
Use the following custom credential format:
user6###MD5###abcdef@123###DES###ghijkl@456
Username: user6
Auth: MD5
Authorization password: abcdef@123
Privacy: DES
Privacy password : ghijkl@456Encoding the Credentials
After formatting the credentials, convert them to Base64 encoding using a tool of your choice.
Example:
Formatted credentials: user6###MD5###abcdef@123###DES###ghijkl@456
Encoded as: dXNlcjYjIyNNRDUjIyNhYmNkZWZAMTIzIyMjREVTIyMjZ2hpamtsQDQ1Ng==.
Configure the Classic Gateway with the Credentials
You can specify multiple SNMPv3 credentials in the gateway configuration file, each on a new line.
- Log in to the gateway using the
ruseraccount. - Open the
/opt/gateway/vprobe/conf/snmp_trap_v3_credentials.cfgfile for editing. - Copy and paste the Base64-encoded credentials into the file.
Note: Refer Adding Custom SNMPv3 Credentials on how to configure SNMP V3 credentials in Base64 encoded format. - Save the file and restart the vprobe service using below command:
service vprobe restart
Your gateway is now set up to process SNMPv3 traps using the configured credentials.
Configure the NextGen Gateway with the Credentials
To configure SNMPv3 trap credentials in the NextGen gateway, follow these steps:
- Create a yaml file and pass the
snmp_v3credentials in a below format.
Example:snmp_trap_v3_credentials: |-snmp_trap_v3_credentials: |- base64EncodedCredkey1 base64EncodedCredkey2 base64EncodedCredkey3
Note
Ensure that there are two spaces under the “snmp_trap_v3_credentials” and then pass the keys after those spaces, as the spaces are necessary for YAML indentation.helm upgrade nextgen-gw oci://us-docker.pkg.dev/opsramp-registry/gateway-cluster-charts/nextgen-gw --version <current_helm_chart_version> -f <YamlFileName> -n <NAMESPACE> --reuse-valuesFAQs
Does OpsRamp generate repeat alerts if the same trap (with the same state) is received?
By default, OpsRamp does not generate repeat alerts for the same trap with the same severity within 30 min. We have an option at OpsRamp’s side where we can enhance trap definition to exclude this 30-min logic in case of valid use cases.
When will OpsRamp exclude/drop any trap with no alerts?
Yes. In 2 cases:
Case 1 - If the trap is in the OpsRamp Global exclude list, then it will not generate any alert.
Case 2 - Client-level Exclude:
If a customer has a trap monitor created in UI
(setup → monitoring → SNMP Traps Configuration) to exclude any specific set of trap(s).
How are trap severities mapped in OpsRamp?
| Actual trap severity | OpsRamp severity |
|---|---|
| Fatal, critical, major, degrade, error, fault, notoperational, shutdown, etc. | Critical |
| Minor, warning, degrade | Warning |
| Ok, info, debug | Ok |