Introduction
Two-factor authentication provides enhanced security by requiring users to confirm their identity using multiple factors, typically a smartphone or email. In addition to user login credentials, users are required to provide a temporary passcode received from the authenticating service. Enabling two-factor authentication is strongly recommended to protect your account from unauthorized access.
To log in using two-factor authentication, a user account must have two-factor authentication enabled and activated using one of the following methods:
- YubiKey: YubiKey is a hardware authentication device manufactured by Yubico that supports one-time passwords, public-key encryption and authentication.
- TOTP: The Time-based One-Time Password (TOTP) algorithm is an extension of the HMAC-based One-time Password algorithm (HOTP) generating a unique one-time password by instead taking uniqueness from the current time. This makes the password valid only for a short time window (usually 30 seconds), enhancing security.
- DUO: The DUO-Security 2nd Factor authentication is a security service offered by Duo Security that adds a second layer of security to keep your account secure. It provides enhanced security by requiring users to confirm their identity using multiple factors, typically a smartphone or email. In addition to user login credentials, users are required to provide a temporary passcode received from the authenticating service.
Enable two-factor authentication
Depending on the authentication scope, use one of the following enablement procedures:
- Enable two-factor authentication for partner or client
- Enable and activate two-factor authentication for users
Enable two-factor authentication for partner or client
Enable two-factor authentication for partner or client from the My Profile screen. When you are done, select from the available two-factor authentication methods the next time you log in.
- After logging into OpsRamp, select Setup → Account.
- From Account Details page, click SETTINGS. The Account Settings page is displayed.
- Select SECURITY tab and under Access Management select the Enable Two-Factor Authentication checkbox.
- Click SAVE to save the changes. The two-factor authentication is enabled.
- To disable the two-factor authentication, clear the Enable Two-Factor Authentication checkbox.
Enable and activate two-factor authentication for users
You can enable and activate two-factor authentication for users to provide high-level account security.
- After logging into OpsRamp, select Setup → Account.
- From Account Details page, select Users and Permissions tile.
- Select Users card. From the Users listing page, search for the user.
- Click the user name.
- On the right-top corner of the page, click the 2FA toggle button to turn it ON.
- Click ACTIVATE. The Activate two-factor authentication popup appears. The options (TOTP, YUBICO, DUO Security) appear based on the options enabled at the partner or client levels respectively.
Note: These three options appear only for self-user (logged-in user). If you are activating them for other users, only YUBICO authentication option appears. - Select an authenticator option, follow the instructions, and click ACTIVATE. The two-factor authentication is activated for the user and you will be logged out automatically.
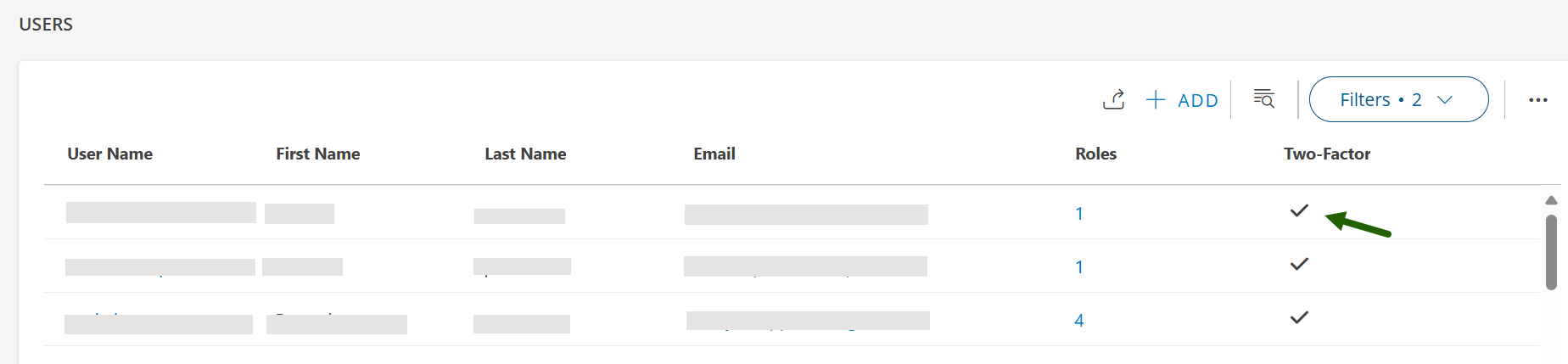
- After successful login, the Two-Factor column on the USERS listing page will display a check mark (✓) indicating that two-factor authentication is active.
Note:
Re-authentication is required after performing one of the following actions:
- Modifying any field in the partner or client Account Settings page.
- Disabling two-factor authentication.
YUBICO authenticator activation
YUBICO Authenticator – A YubiKey is a small hardware device that offers two-factor authentication with a simple touch of a button.
- After logging into OpsRamp, select Setup → Account.
- From Account Details page, select Users and Permissions tile.
- Select Users card. From the Users listing page, search for the user.
- Click the user name.
- On the right-top corner of the page, click the 2FA toggle button to turn it ON.
- Click ACTIVATE. The Activate two-factor authentication popup appears.
- Select YUBICO Authenticator.
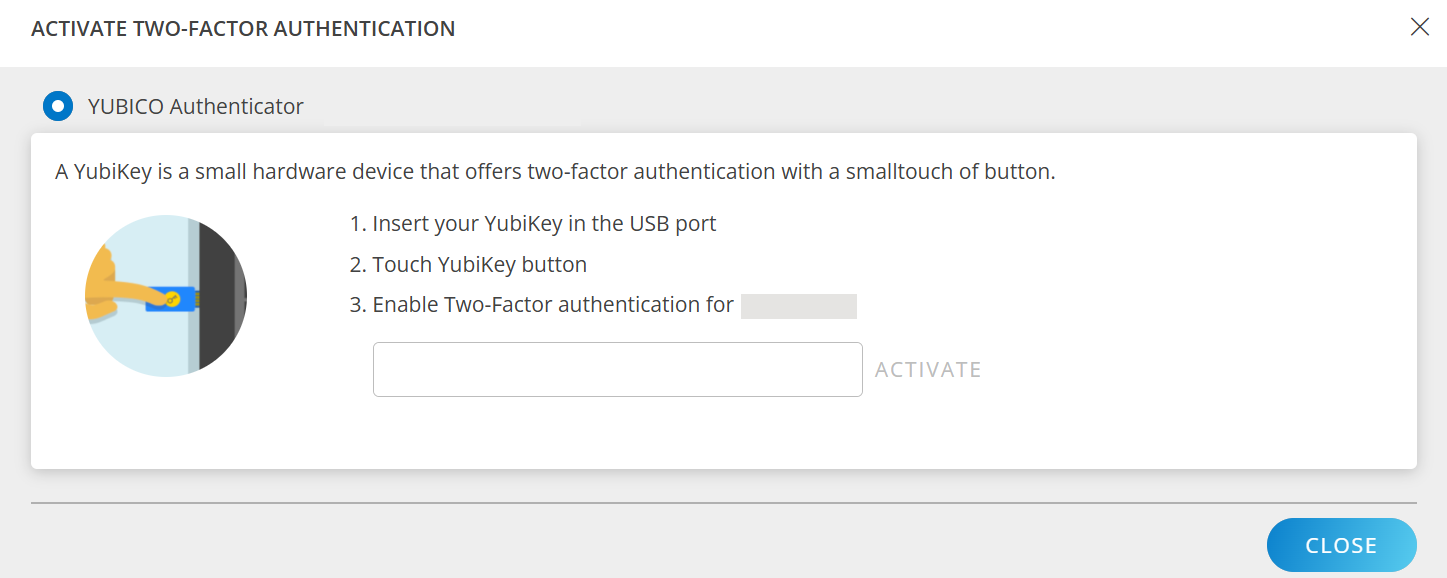
- Follow the instructions, and click ACTIVATE.
The two-factor authentication is activated and you will be logged out automatically.
After successful login, the Two-Factor column on the USERS listing page will display a check mark (✓) indicating that two-factor authentication is active.
TOTP authenticator activation
TOPTP Authenticator – Time-based One-time Password Algorithm (TOTP) is an algorithm that computes a one-time password from a shared secret key and the current time.
Before activating a TOTP authenticator, install a third-party application that supports TOTP on your smartphone. The application generates login passcodes and can receive push notifications for one-tap authentication.
The following applications support TOTP: - Google Authenticator - Windows Authenticator - DUO Authenticator - Authy Authenticator
- After logging into OpsRamp, select Setup → Account.
- From Account Details page, select Users and Permissions tile.
- Select Users card. From the Users listing page, search for the user.
- Click the user name.
- On the right-top corner of the page, click the 2FA toggle button to turn it ON.
- Click ACTIVATE. The Activate two-factor authentication popup appears.
- Select TOTP Authenticator.
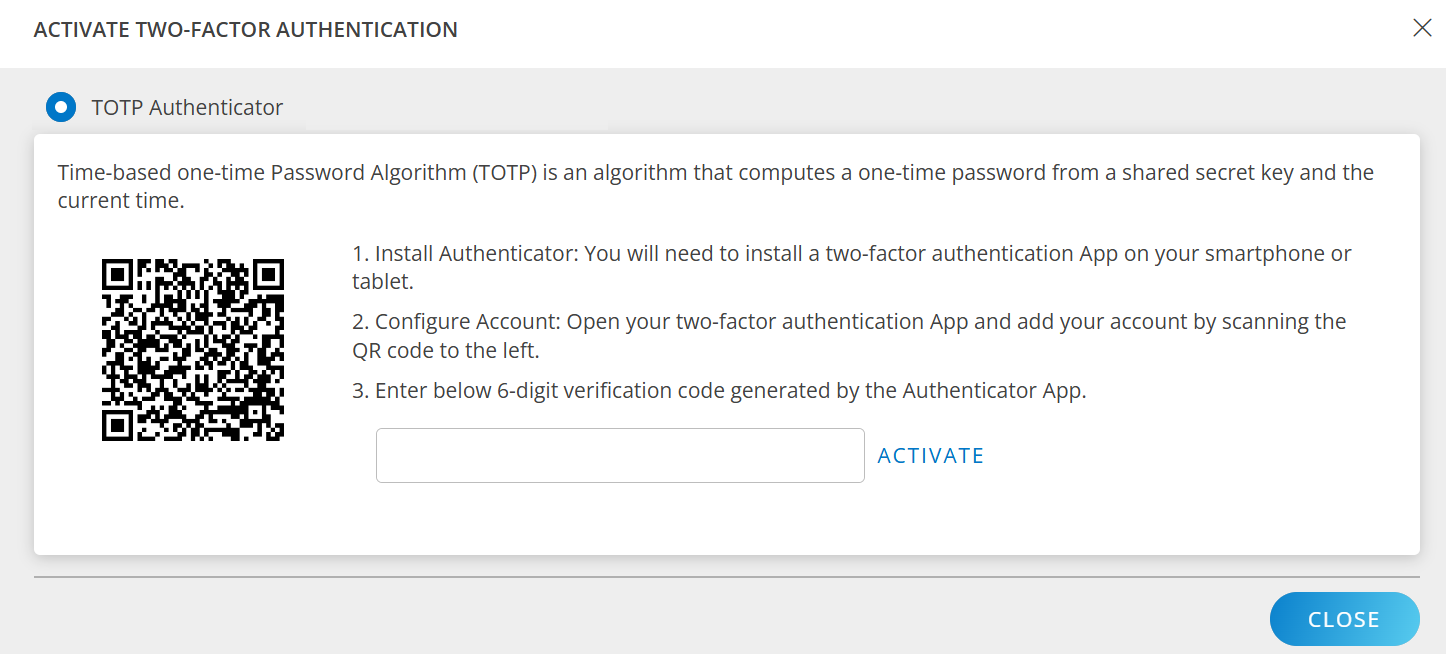
- Follow the instructions, and click ACTIVATE.
The two-factor authentication is activated and you will be logged out automatically.
After successful login, the Two-Factor column on the USERS listing page will display a block mark indicating that two-factor authentication is disabled.
Disable two-factor authentication
Disabling two-factor authentication (2FA) removes the additional layer of security from your account, making it accessible with just a username and password. This action should be performed with caution, as it reduces protection against unauthorized access. Re-authentication is required after disabling 2FA to ensure the change is authorized.
You can disable two-factor authentication from the USERS details page or My Profile page.
- After logging into OpsRamp, select Setup → Account.
- From Account Details page, select Users and Permissions tile.
- Select Users card. From the Users listing page, search for the user.
- Click the user name.
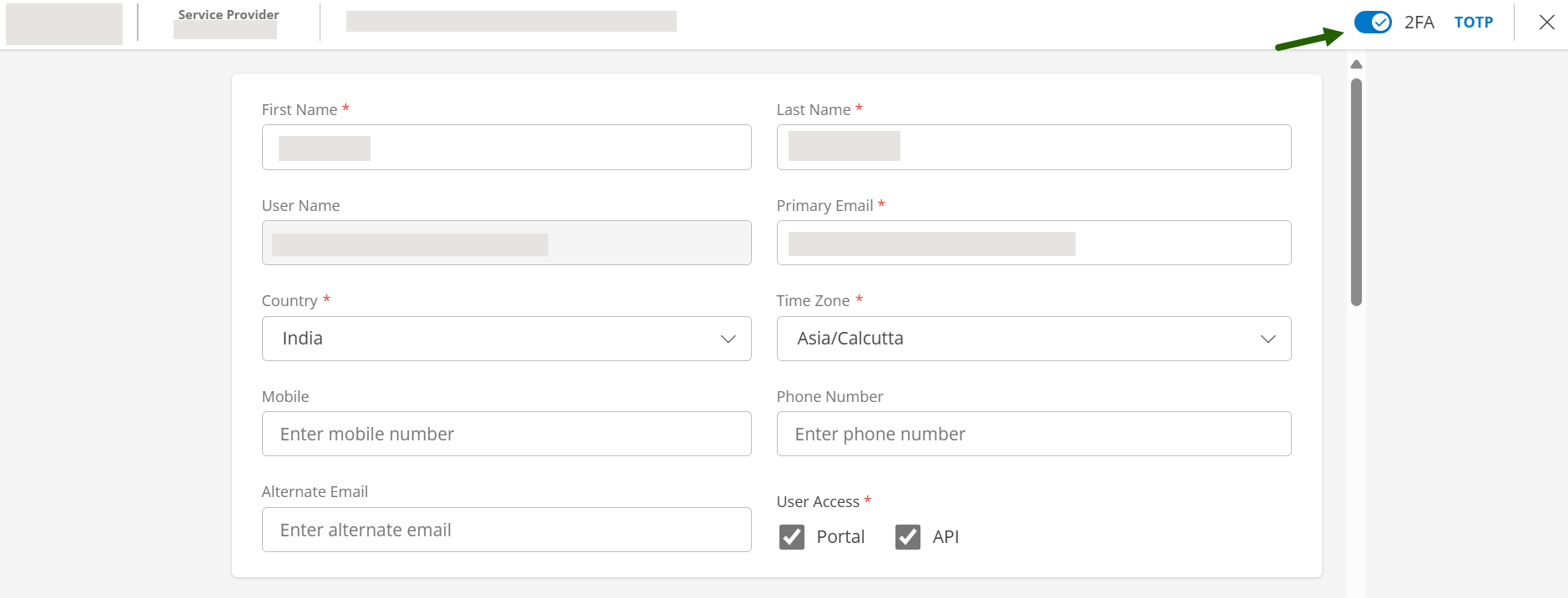
- Click the 2FA toggle button to turn it OFF.
- Follow the steps to validate the authentication and click VALIDATE.
The two-factor authentication is disabled and you will be logged out automatically.
After successful login, the Two-Factor column on the USERS listing page will display a block mark indicating that two-factor authentication is disabled.![]()
Log in using two-factor authentication
If two-factor authentication is activated for your account, you are required to take the step of providing a passcode after entering your username and password.
On three failed attempts to enter the correct passcode, you are routed to the login page to reenter your username and password.
Log in using YubiKey
- Insert the YubiKey into the USB port on the device.
- Log in using your username and password credentials.
- After you log in, in the YubiKey login, touch the YubiKey button. A 44-character, one-time passcode is generated.
Log in using TOTP
TOTP login requires a smartphone to log in.
- Log in using your username and password credentials.
- Enter the 6-digit scanned verification code. The code expires after 60 seconds before generating a new verification code. Log in is successful.
Lost two-factor key
Follow the below steps to find the owner of a lost two-factor key:
- After logging into OpsRamp, select Setup → Account.
- From Account Details page, select Users and Permissions tile.
- Select Users card.
- From the USERS listing page, click the ellipsis (three dots) icon and select Lookup Two-Factor Key.
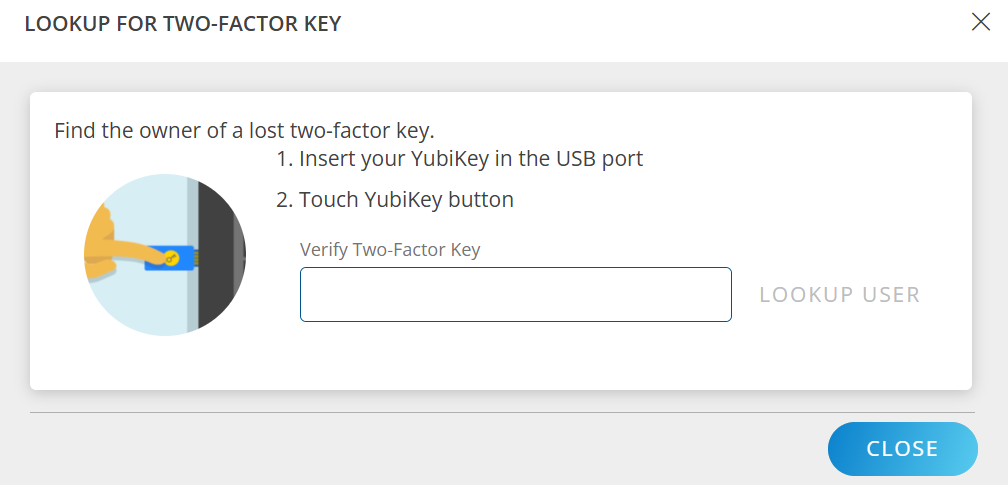
- Follow the instructions and click LOOKUP USER. User details are displayed.