SSO integration configuration involves both Okta and OpsRamp platforms to configure redirects to your custom branding URL.
Prerequisites
- Partners register with OpsRamp to get login credentials.
- Provide a custom branding URL, such as
.opsramp.com.
Configure Okta SSO integration
Select Applications from the Applications menu.
Search for the OpsRamp app and click the Add button.
On the Add OpsRamp page in the General Settings - Required section, enter the website subdomain in the Subdomain field.
You can find the subdomain on the Accounts > Clients page in the subdomain part of the Website URL. For example, it is the
okta-certpart ofokta-cert.app.opsramp.com.Click Done.
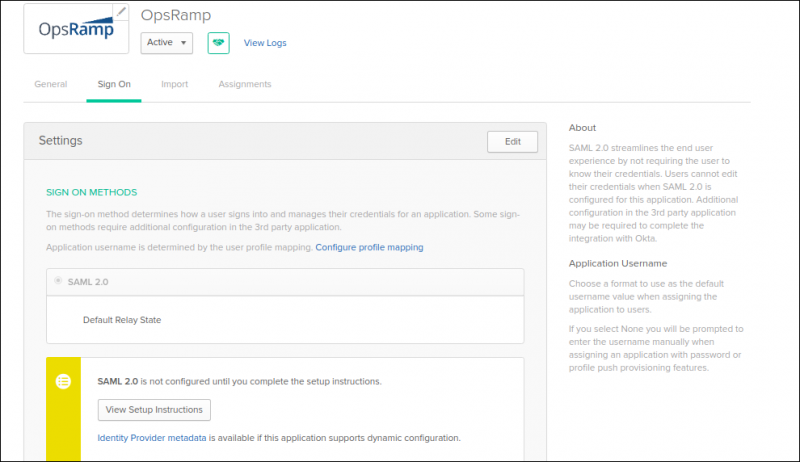
From the Applications menu, select the OpsRamp app and review the settings on the Sign On tab.
Select View Setup Instructions and configure the following:
- Okta instructions Issuer URL
- Redirection URL
- Logout URL
- Certificate
Single Sign-On Settings
OpsRamp Configuration
From All Clients, select a client.
Navigate to Setup > Account.
Select the Integrations and Apps tab.
The Installed Integrations page, where all the installed applications are displayed. Note: If there are no installed applications, it will navigate to the Available Integrations and Apps page.
Click + ADD on the Installed Integrations page. The Available Integrations and Apps page displays all the available applications along with the newly created application with the version.
Search for Okta using the search option available. Alternatively, use the All Categories option to search.
Click +Add on the Okta tile.
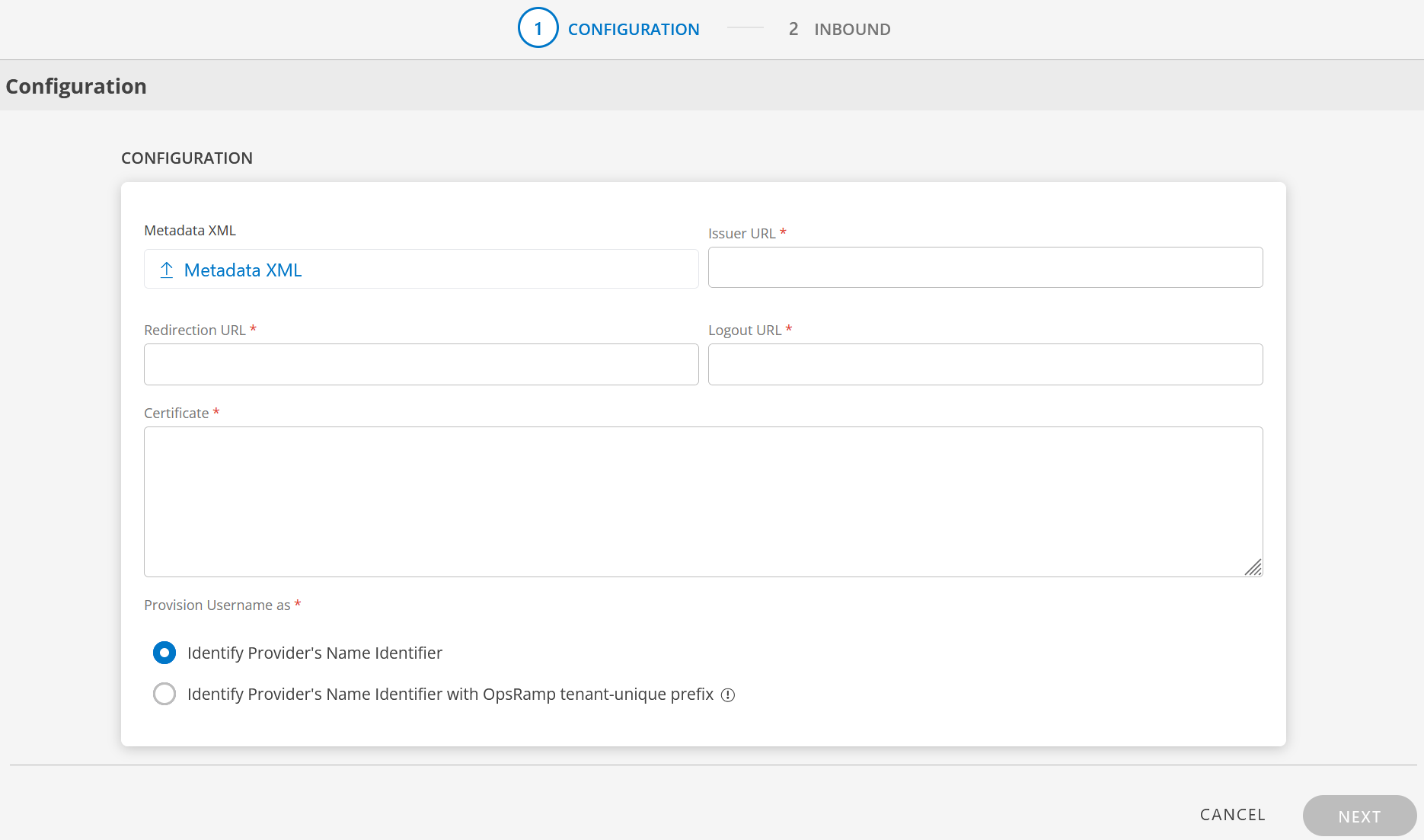
Enter the following information in the Configuration page:
- Metadata XML: Upload the XML file. This file will have all the information related to Issuer URL, Redirection URL, Logout URL, and Certificate. After you upload the Metadata XML file, these fields are automatically populated.
Alternatively, you can enter the information in the fields manually. - Issuer URL: Identity provider Issuer URL
- Redirection URL: SAML EndPoints for HTTP
- Logout URL: URL for logging out
- Certificate: x.509 Certificate
- Metadata XML: Upload the XML file. This file will have all the information related to Issuer URL, Redirection URL, Logout URL, and Certificate. After you upload the Metadata XML file, these fields are automatically populated.
Provision Username as: There are two ways to provision a user. Select the appropriate option:
Identify Provider’s Name Identifier option is selected by default. The user which is created in the SSO portal will reflect in OpsRamp.
Identify Provider’s Name Identifier with OpsRamp tenant-unique prefix: This option allows you to:
- Create usernames with a unique 3-digit alphanumeric prefix, that is generated automatically by the system.
- Install the same identity provider across multiple OpsRamp tenants.
Note: Once you enable this option and install the integration, you cannot revert your changes.
Example: There are three partners, Partner P1, P2, and P3. Each partner has usernames created with unique 3-digit alphanumeric prefix, like g0z.username1 for partner P1, p0w.username1 for partner P2, and t9q.username1 for partner P3.
Click Next.
In the Inbound page, there are two sections: USER PROVISION and MAP ATTRIBUTES.
USER PROVISION
OpsRamp supports two user provisioning methods to onboard users from identity providers like Okta:
SCIM
Following section describes SCIM provisioning in detail.
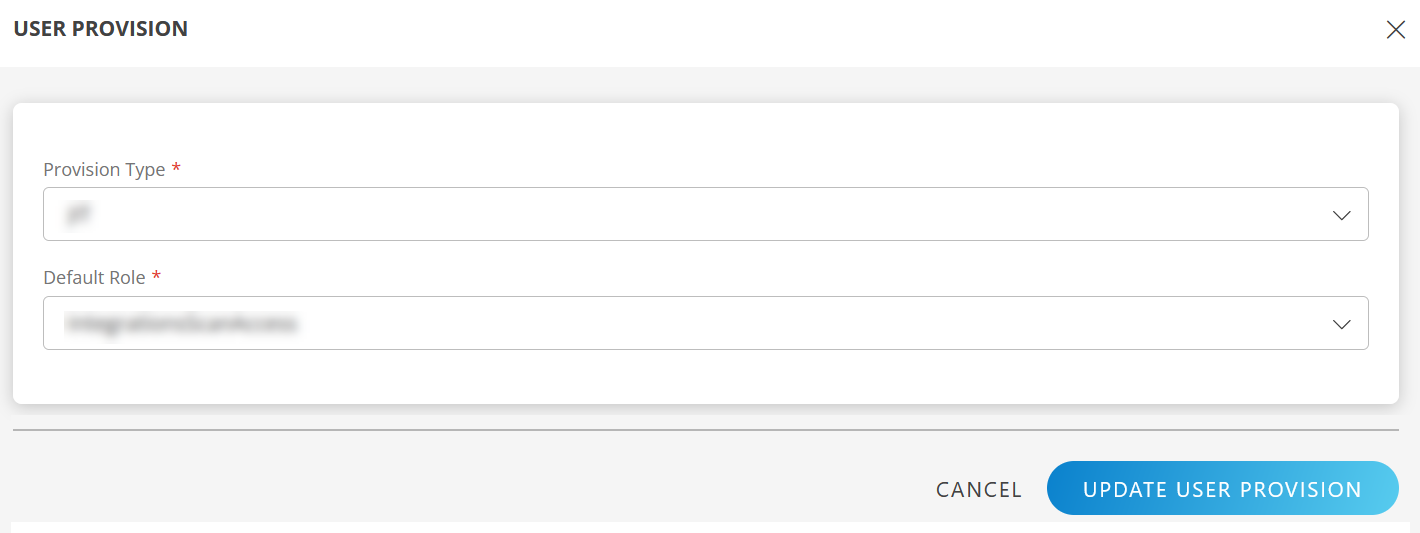
Click Edit icon and select the following details and click UPDATE USER PROVISION:
- Provision Type: SCIM. When configuring the integration it is necessary to select the Provision Type - SCIM to synchronize users and groups when provisioning occurs.
- Default Role: The required user role.
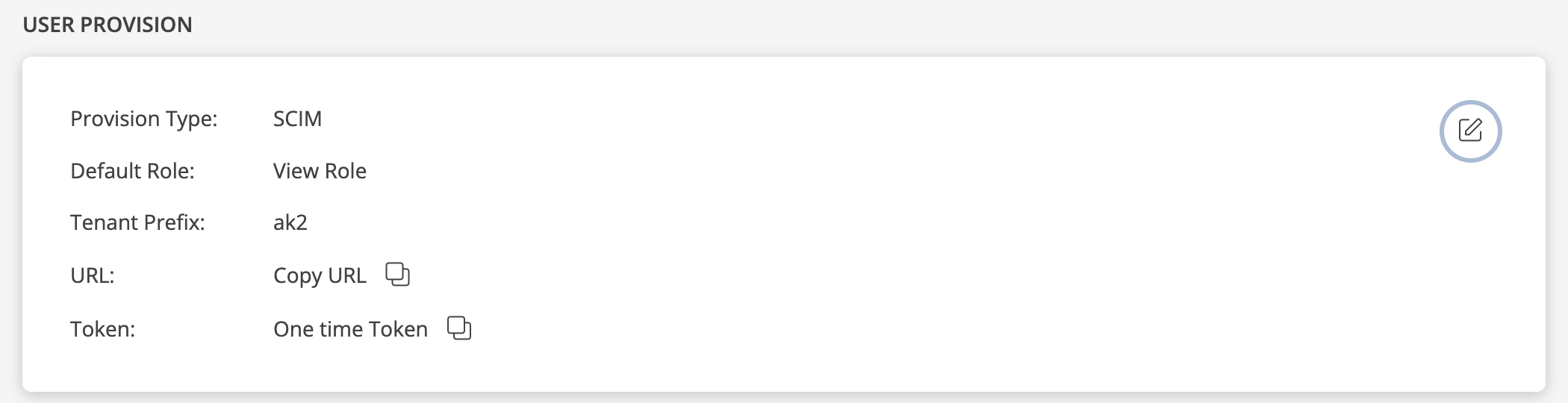
The details are updated and the USER PROVISION section displays the unique Tenant Prefix, URL and Token information.
Copy the URL and Token information. These details are used when configuring Okta Provisioning settings.
MAP ATTRIBUTES
Define the following Map Attributes:
Note:
- For SCIM: The Role OpsRamp property is required.
- For JIT: The OpsRamp properties like Primary Email, First Name, Last Name, and Role are required.
- Click +Add in the Map Attributes section.
- From the Add Map Attributes window, enter the following information:
User:
- Select OpsRamp Entity as User and OpsRamp Property as Role.
Role mapping is required for User and User Group.
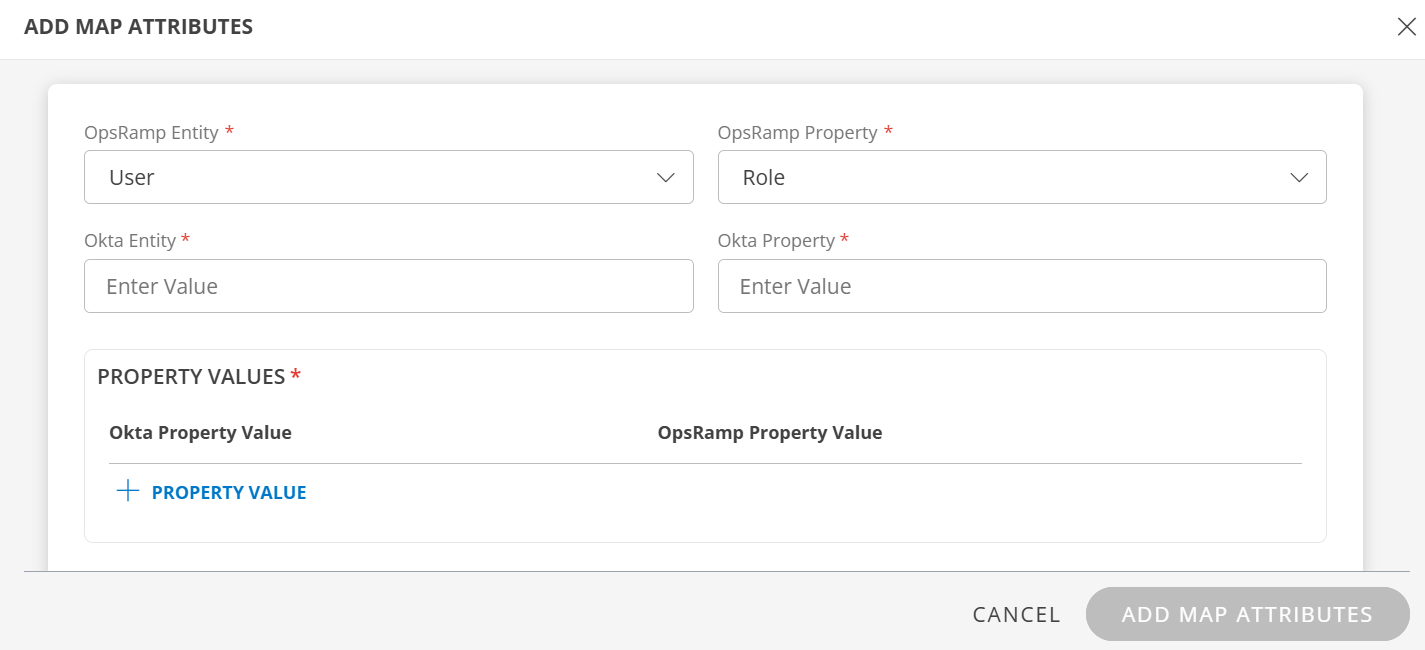
- Okta Entity: Enter the value.
- Okta Property: Enter the value.
In PROPERTY VALUES section: - Okta Property Value: The user details in the request payload received by OpsRamp contains the field information. Ensure that you provide the value of the field in this box.
- Example payload:
{ "schemas": [ "urn:ietf:params:scim:schemas:core:2.0:User" ], "userName": "user.name1@opsramp.com", "name": { "givenName": "user", "familyName": "name1" }, "emails": [ { "primary": true, "value": "user.name1@opsramp.com", "type": "work" } ], "phoneNumbers": [ { "primary": true, "value": "1234567890", "type": "work" } ], "addresses": [ { "primary": true, "country": "IN" } ], "timezone": "india", "externalId": "00upcikgqpH6esdAN0h7", "groups": [], "password": "o6p5MVRK", "active": true } - OpsRamp Property Value: Select the appropriate role corresponding to the Okta Property Value.
- Click Save. The mapping is saved and displayed.
To add more property values click +Property Value.
User the Filter option to filter the map attributes.
Similarly, map attributes for other entities.
Note: If mapping for Time Zone is not provided, then organization timezone is considered by default.
User Group:
- Select OpsRamp Entity as User Group and OpsRamp Property as Role.
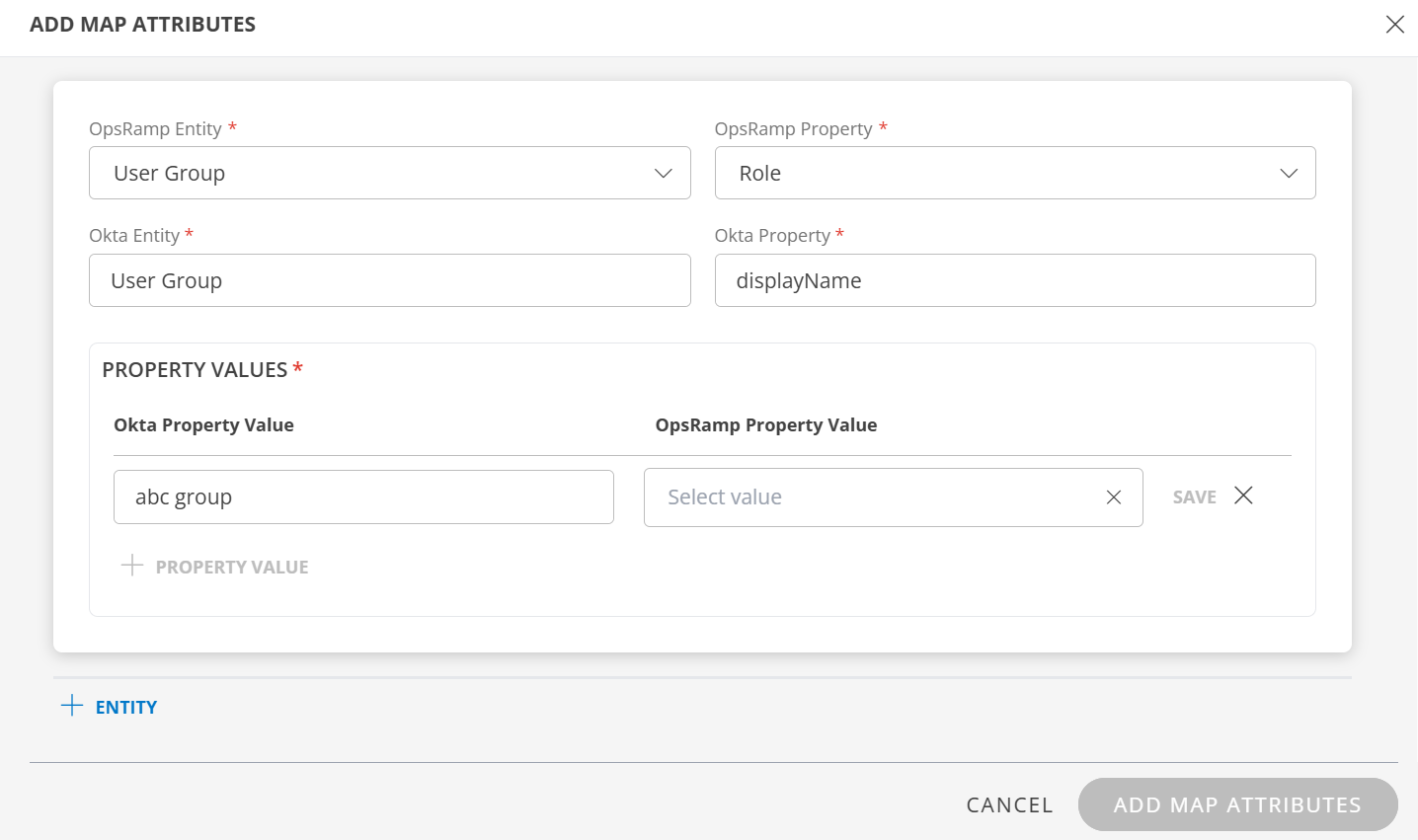
- Okta Entity: Enter the value.
- Okta Property: Enter the value.
In PROPERTY VALUES section: - Okta Property Value: The user group details in the request payload received by OpsRamp contains the field information. Ensure that you provide the value of the field in this box.
- Example payload:
{ "schemas": [ "urn:ietf:params:scim:schemas:core:2.0:Group" ], "displayName": "abc group", "members": [ { "value": "USR0002265918", "display": "user.name1@opsramp.com" }, { "value": "USR0002398463", "display": "user.name2@opsramp.com" } ] }In this case, you enter abc group as value. If there is a match, OpsRamp provisions the user group accordingly.
- OpsRamp Property Value: Select the appropriate role corresponding to the Okta Property Value.
- Click Save. The mapping is saved and displayed.
To add more property values click +Property Value. - Click Add Map Attributes.
- Click the three dots (menu icon) available at the end of each row to edit or delete a map attribute.
If the Role is not configured in Map Attributes section, the Default Role provided in the User Provision section is considered for SSO.
JIT
Following section describes JIT provisioning in detail.
In the Inbound page:
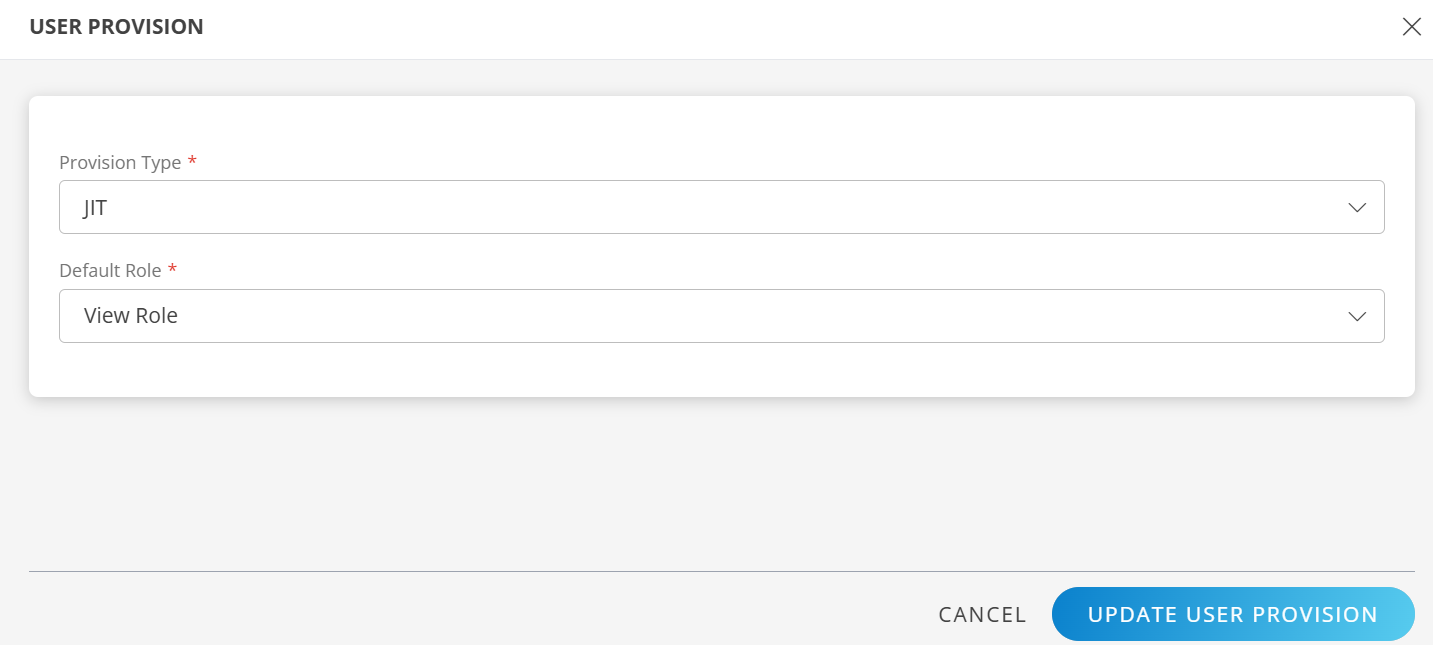
- Click Edit icon and select the following details and click UPDATE USER PROVISION:
- Provision Type: JIT. When configuring the integration it is necessary to select the Provision Type - JIT to synchronize users when provisioning occurs.
- Default Role: The required user role.
The details are updated and the USER PROVISION section displays the unique Tenant Prefix. These details are used when configuring Okta Provisioning settings.
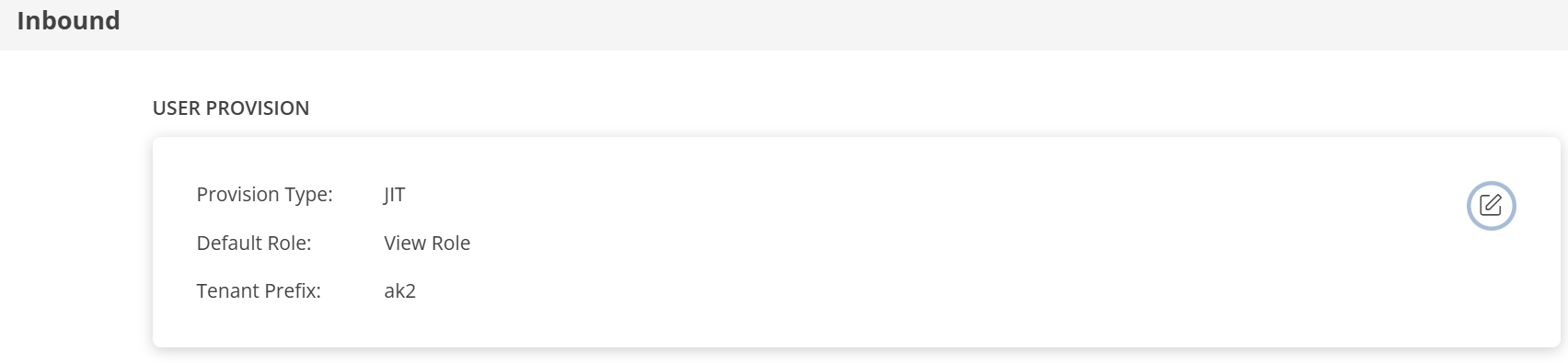
Follow the steps mentioned in the MAP ATTRIBUTES section above, to define the Map Attributes.
Click Finish. The integration is installed.
Actions on Integration
You can perform actions like View Logs, Export, Edit, and Uninstall on the integration.
- See Actions on Integration for more information.
Audit Logs
View Inbound logs from the View Logs option for the integration. You can view if the event was successful or not.
See Audit Logs for more information.
Verification SSO integration
- From the Okta console, go to the OpsRamp Application.
- Click Sign On, and click View Setup Instructions.
- Verify the following settings:
- Issuer URL: Identity Provider Issuer URL
- Redirection URL: Identity Provider SSO URL
- Logout URL: URL for logging out
- Certificate: x.509 Certificate
Provision a user
After configuring the OpsRamp-Okta integration, you can provision users.
In the OpsRamp UI …
- Navigate to the Accounts > Clients page.
- Click Okta client and copy the subdomain part of the Website URL, which you need to specify the subdomain in Okta. For example, copy the
okta-certpart ofokta-cert.app.opsramp.com.
Prepare to install.
- In Integrations > Integrations, click the SSO button to display the available SSO integrations.
- Click the Okta icon.
- Click the Install button. Continue on the Okta to get the integration parameters needed.
On the Okta console …
Enter the OpsRamp subdomain:
- Select Applications from the Applications menu.
- Click the Add button.
- On the Add OpsRamp page in the General Settings - Required section, enter the website URL copied from OpsRamp in the Subdomain field:
okta-cert. - Click Done.
Set up the sign-on method:
Select Applications from the Applications menu.
Select the Sign On tab.
Scroll down and click the View Setup Instructions button to configure SAML 2.0 for OpsRamp.
From step six of the setup instructions, copy and save the values in the following fields:
- Issuer
- redirection URL
- logout URL
- certificate
In the OpsRamp UI …
- Returning to the Install Okta Integration screen, enter the information copied from Okta:
- Issuer URL
- Redirection URL
- Logout URL
- Certificate
- Click Install
- On the OKTA INTEGRATION page Configuration tab Properties section, verify the Issuer URL, Redirection URL, and Logout URL. The Provision Type should be SCIM.
- In the User Provision section, copy and save the URL and Token for the Okta base URL and API token fields.
On the Okta console …
Provision the user:
- On the Applications > Integration page, click the Provisioning tab.
- Scroll down and click Configure API Integration.
- Select Enable API integration.
- Enter the Base URL and the API Token copied from OpsRamp instructions.
- Click Test API Credentials. Successful credential verification displays the OpsRamp was verified successful! message.
- Click Save. On success, Provisioning settings saved! is displayed.
Add a user.
- Click the Assignments tab.
- Open another Okta console in a new tab and navigate to Directory > People.
- Click Add Person
- Enter the required and any optional personal information in the provided fields. The Username must be an email address.
- For the Password field, choose Set by admin and enter a password.
- Click Save. A Person added! message displays.
Enable user provisioning.
Navigate to Applications > Applications and choose the Provisioning tab.
In the Provisioning to App panel, click Edit.
Select Create User - Enable, Update User Attributes - Enable, and Deactivate Users - Enable.
Select the following Enable options to complete the provisioning setup.
- Create Users
- Update User Attributes
- Deactivate Users
Click Save and wait for application setup verification. On success, a Provisioning settings saved! message displays.
Assign the OpsRamp application to the user.
- Return to the first tab and, from the Assign drop-down menu, choose Assign to People.
- Use the search bar to search for the user you added in the other Okta console.
- Find the entry for the user from the search results and click Assign.
- In the Assigned Applications section, click the Assign Applications button.
- Click OpsRamp in the application list.
- In the Applications > Assignments tab, click the Assign button and choose Assign to People.
- Find OpsRamp in the list and click Assign.
- For the user you want to assign to the OpsRamp application, click Assign.
- Edit the user information field you want to change and click Save and Go Back.
- Click Done to complete assigning users. The 1 person assigned successfully message displays.
In the OpsRamp UI …
Navigate to Accounts > Users and, after a short delay, see that the provisioned Okta user is added to the user list.
Unprovision a user
On the Okta console …
- Choose the Assignments tab.
- Click the X for the user to delete in the user list.
- Click OK to confirm that you want to unassign the user.
In the OpsRamp UI …
Refresh the Accounts > Users page to confirm the user is deleted from the list.
Notes:
- Changes to the token used in the SCIM user provision case should not be changed since it will prevent users from being updated or created.
- Username created should be unique across clients.